Prisma
Cloud
Cloud secures hybrid
& multi-cloud environments
Prisma
Cloud
Cloud secures hybrid
& multi-cloud environments
Cloud computing security refers to a broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructures of cloud computing.
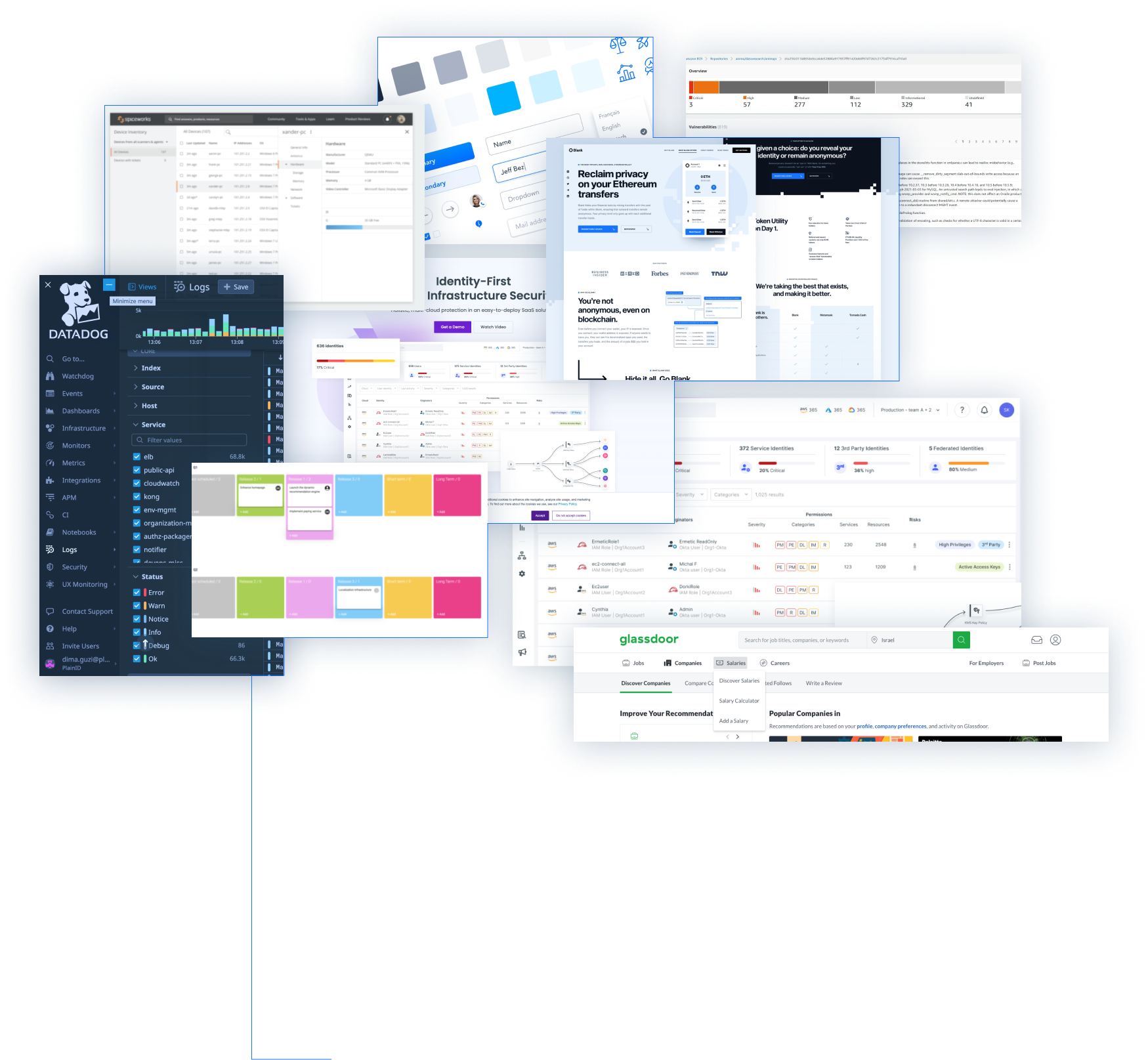
In this project, I focused on creating a flow for a monitoring system that identifies security weaknesses and protects if needed
Security and DevOps teams are facing the challenge of monitoring unprotected systems while building and deploying in multi environments
complete security across the development lifecycle on any cloud
What challenges face
security developers?
Shilla, 38, DevOps developer,
uses Prisma Cloud software on
a daily basis constantly monitors services, identifies and protects security vulnerabilities
Proper utilization of services is
an integral measure of a product’s success
“
User’s pain points
How can the workflow of
a developer be improved?
Creating an
up-to-date,
flexible
workspace
Unprotected
systems must
be located
quickly
Continual alerts
for all cloud
environments
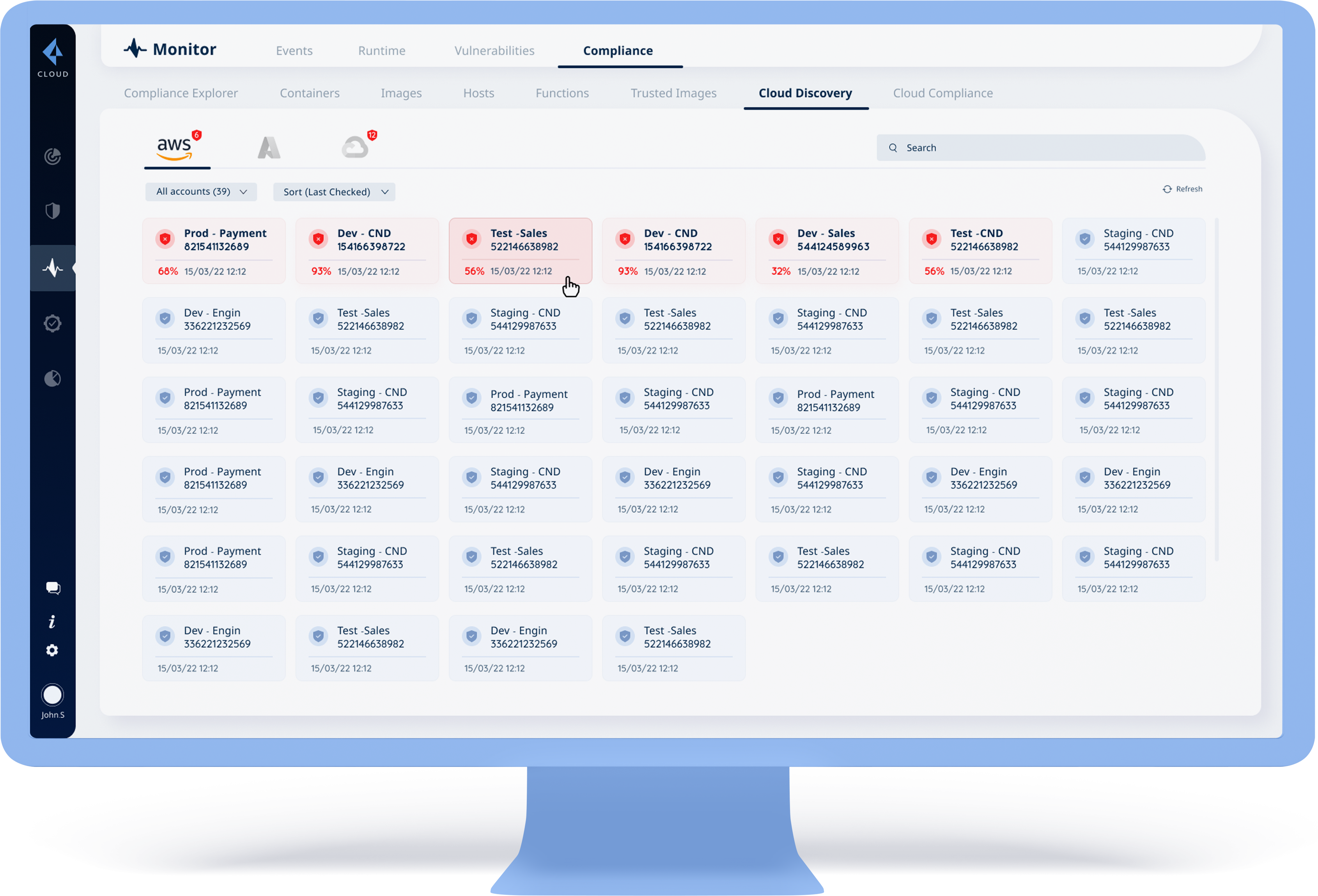
Unprotected systems will appear first by default
Systems that are partially protected will appear as “unprotected,” and the protection level as a percentage
Items and failed systems will be reported even in parallel environments
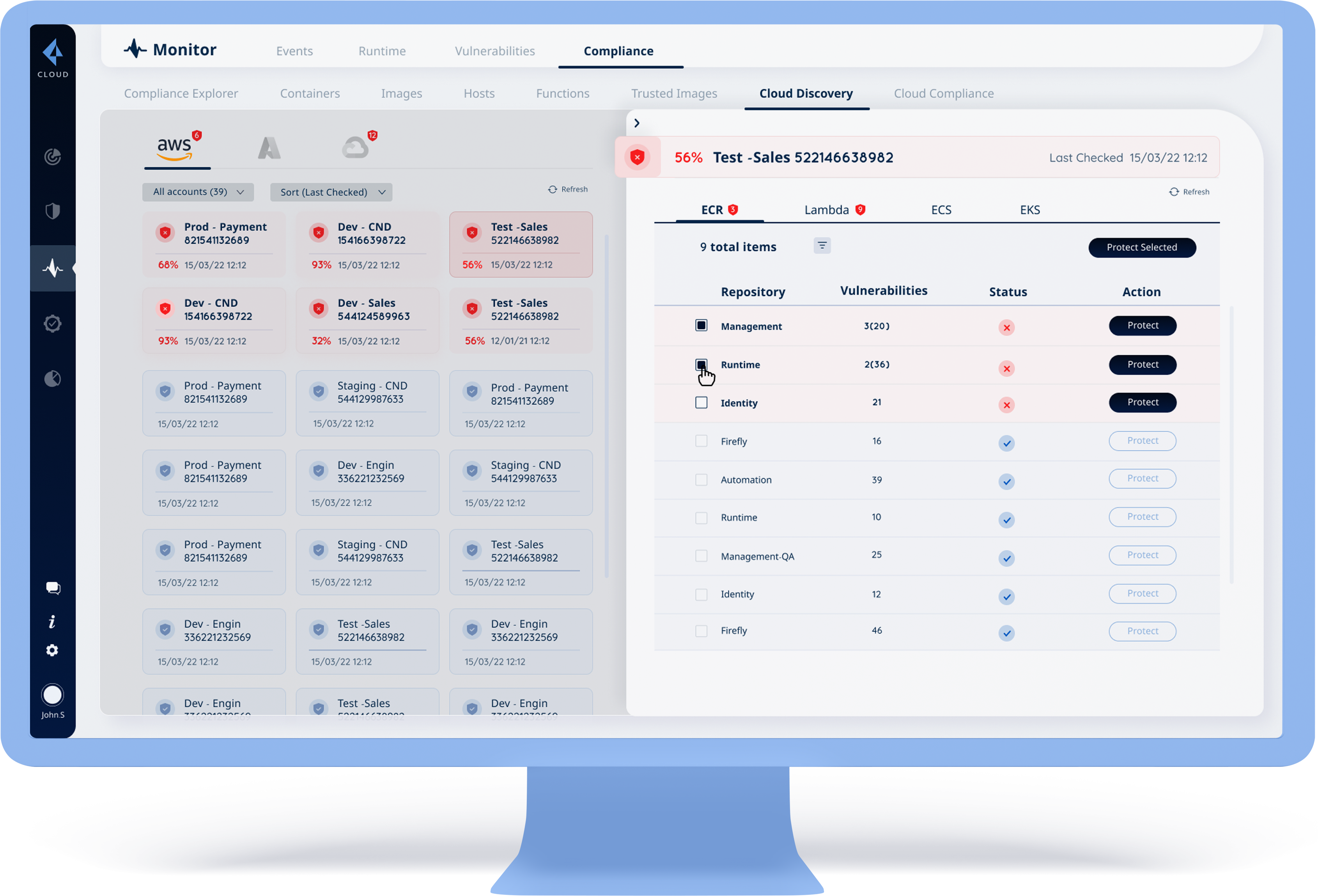
Multiple choices will be offered for unprotected systems and collective protection
Support communication between developers working on the same dashboard
Transparency and central feed in all categories to enhance control and orientation
A central search bar by name, date, urgency, etc., along with options for sorting and filtering for accurate results
Easily change workspaces manually by creating a flexible workspace
Product main navigation has 5 sections:
Radar | Defend | Monitor | Manage | Segment
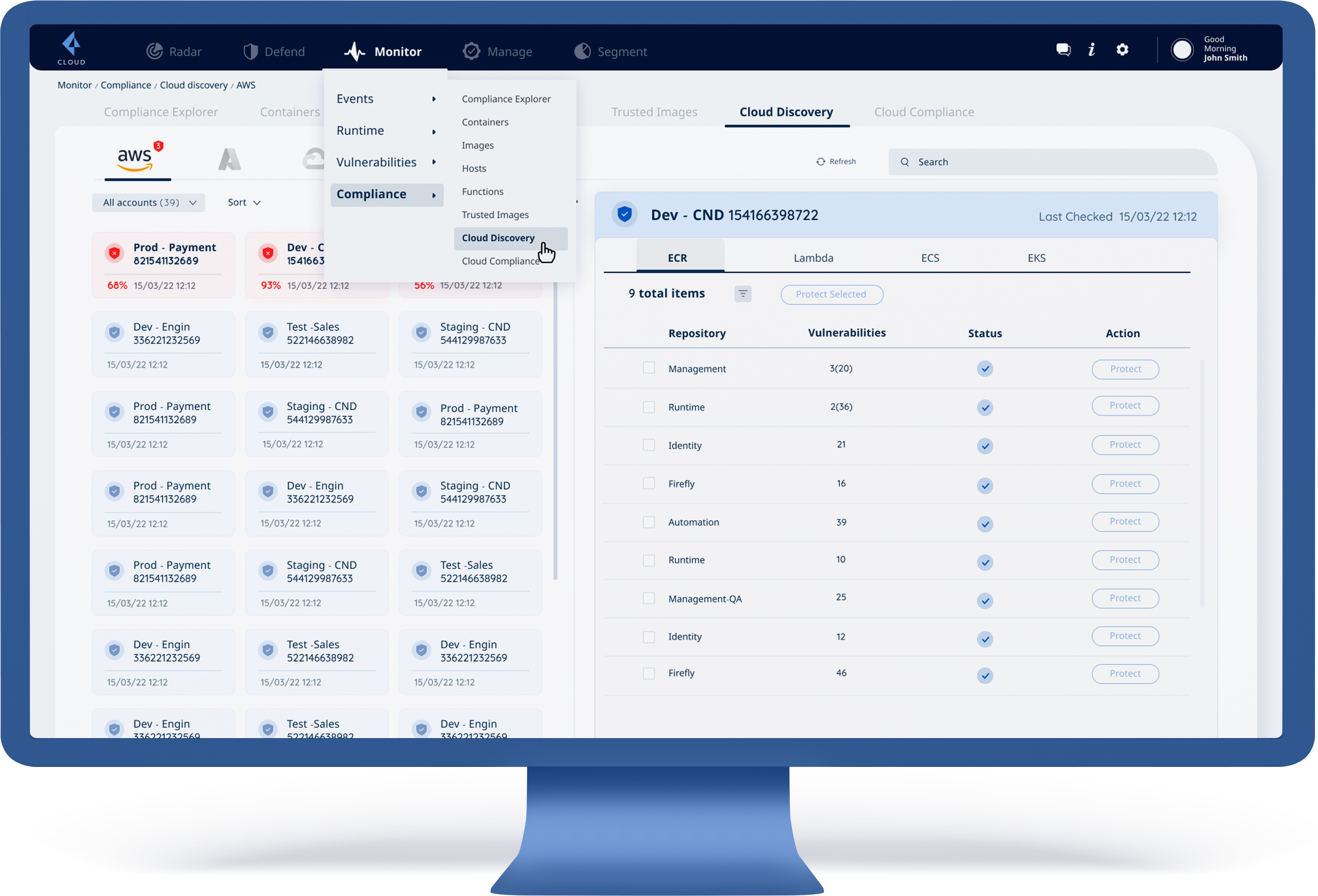
Focus on the Monitor section, which has these categories:
Events | Runtime | Vulnerabilities | Compliance
Focus on the Compliance category
The compliance category has 7 subcategories:
Compliance Explorer | Containers | Images | Hosts | Functions
| Trusted Images | Cloud Discovery | Cloud Compliance
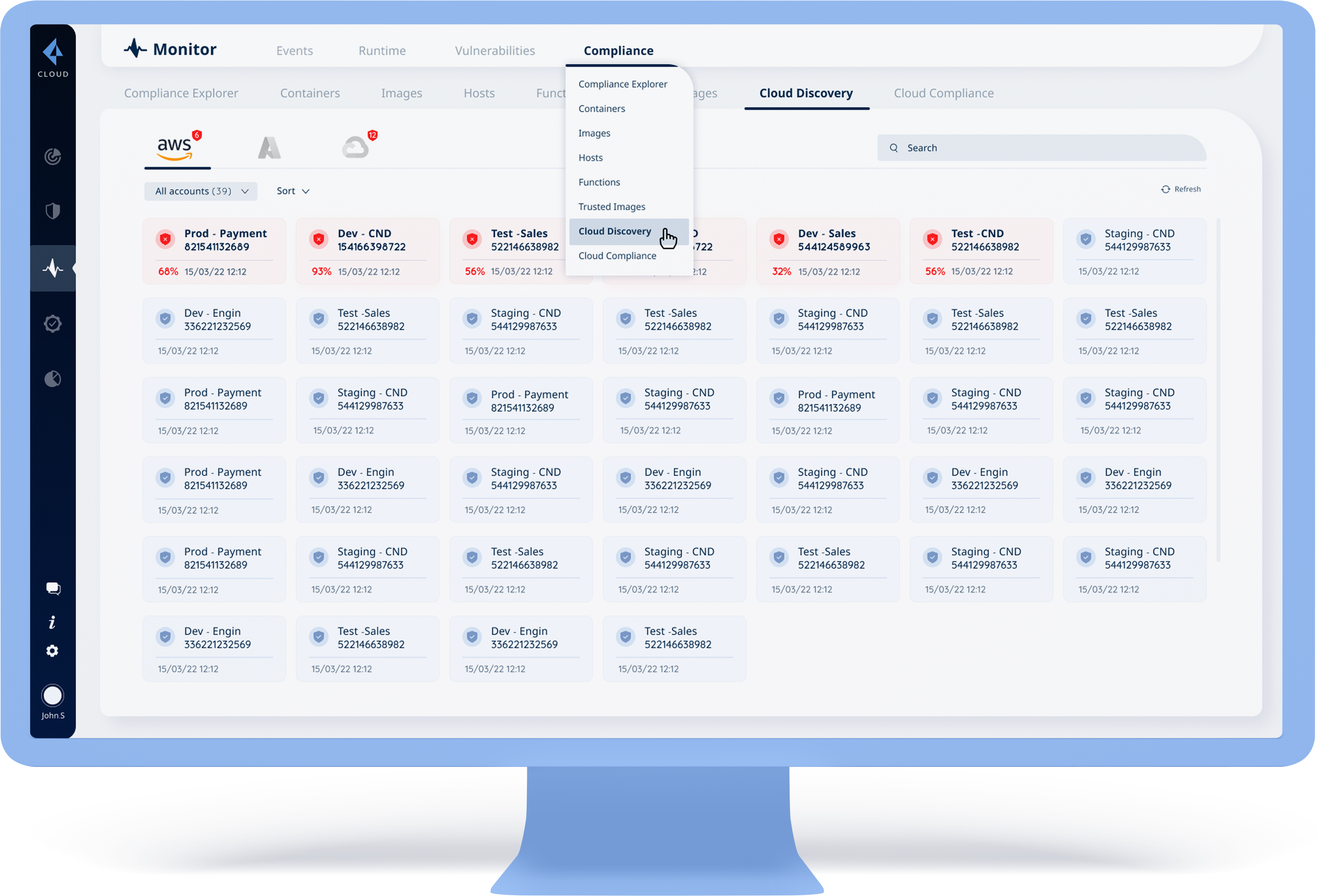
Focus on the last one: Cloud Discovery. Under this subcategory we will have 3 different cloud providers:
AWS | Azure | GCP
Focus on the first one: AWS
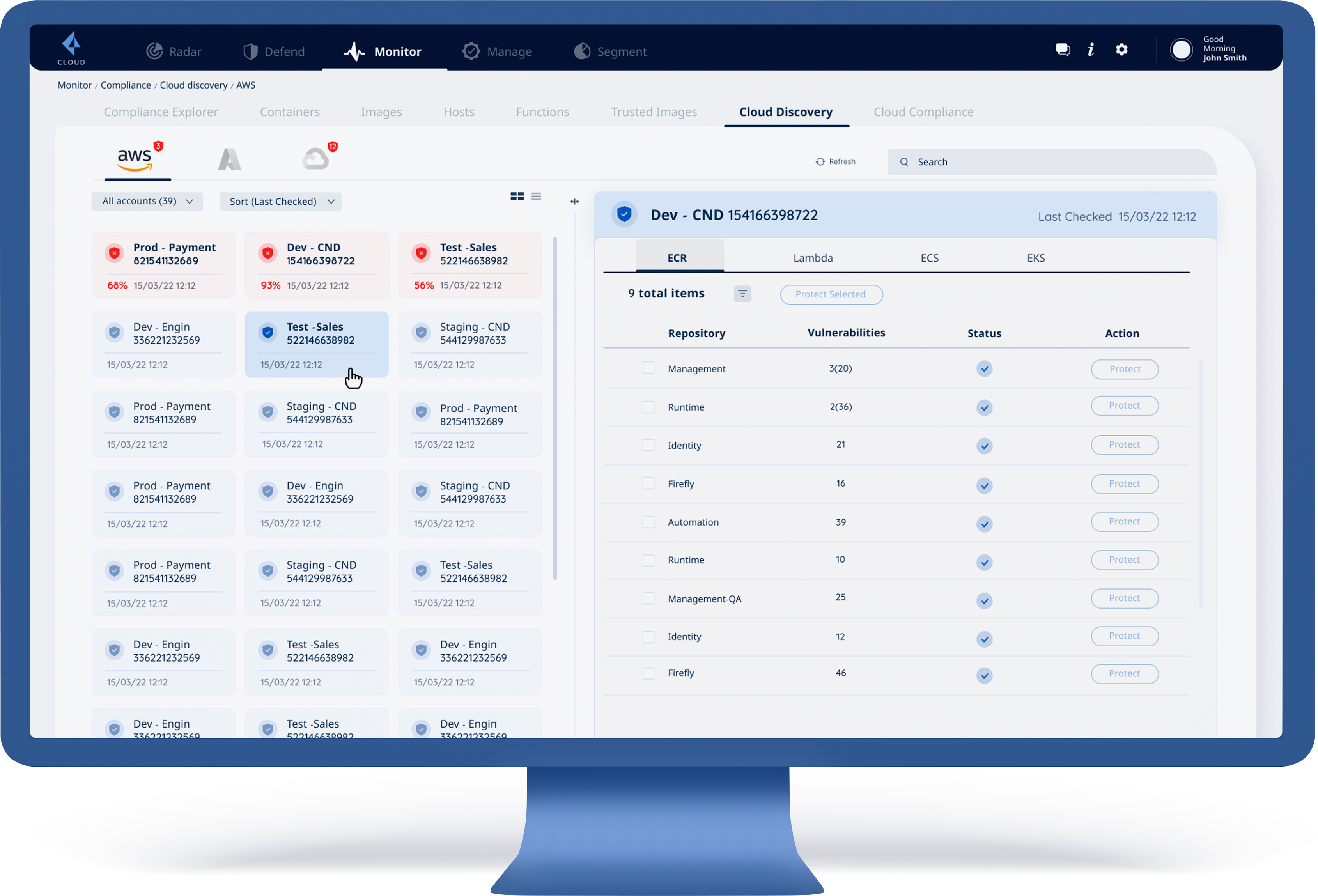
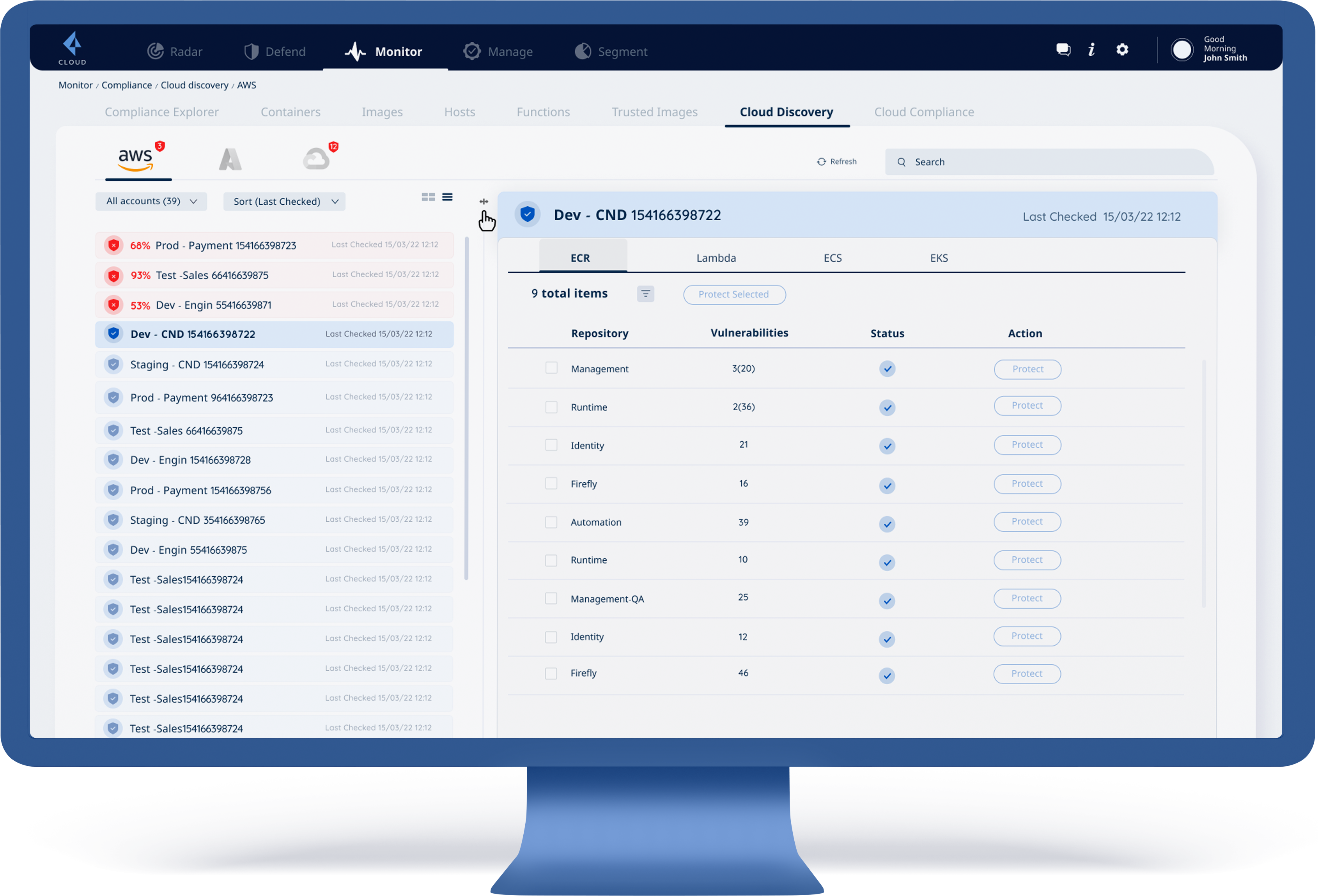
Select an account in which we want to review its status:
protected / unprotected
(There are usually many accounts to choose from between 1-100 for example)
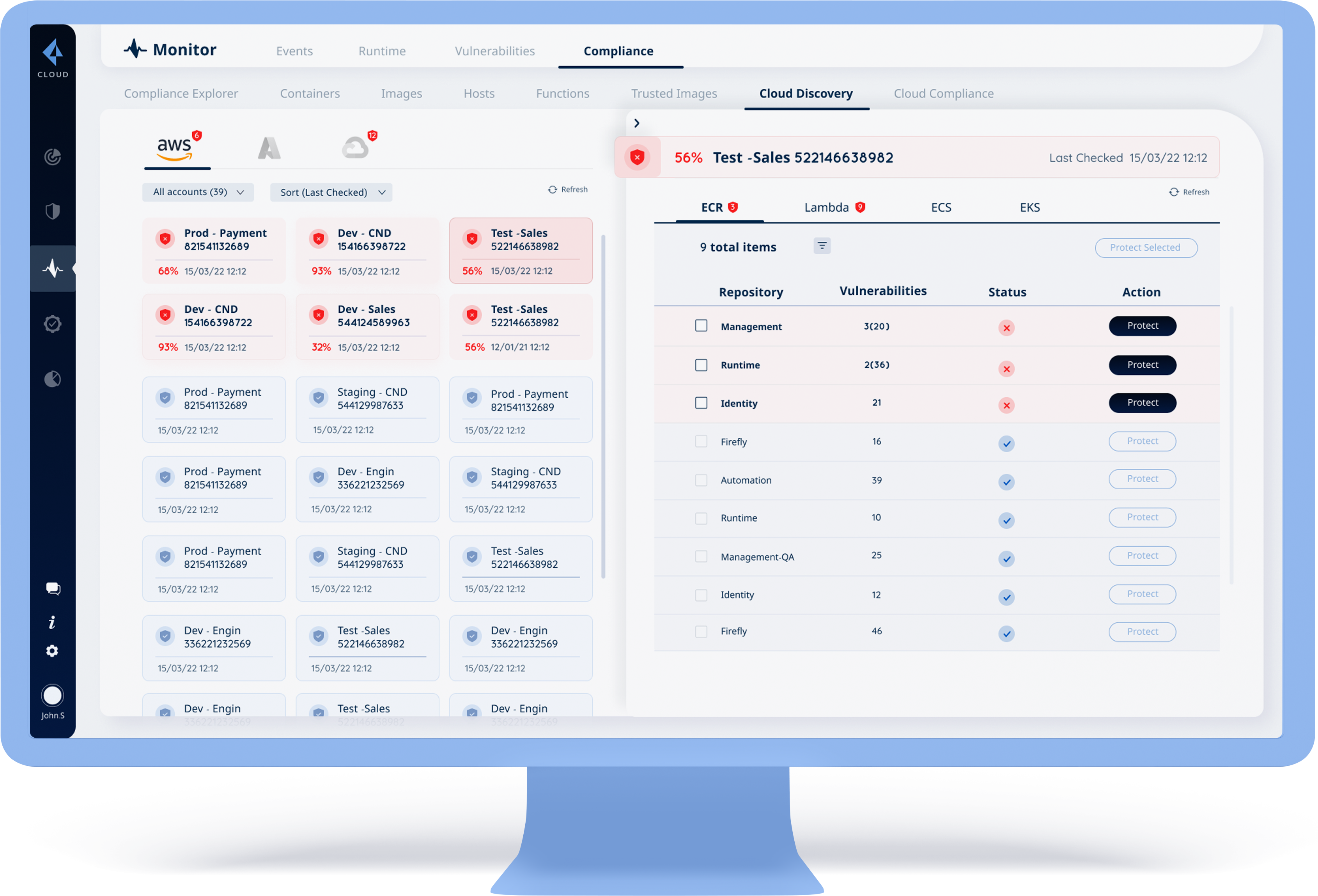
After selecting an account, we will show 4 types of apps under the AWS cloud:
ECR | Lambda | ECS | EKS
Each one of these types of AWS cloud will show:
The number of total items | List of the items | Status of these items: protected/unprotected